US And Europe Try To Tame Surveillance Capitalism

Feature The US Federal Trade Commission on Monday warned that data brokers need to rethink how they define sensitive data in light of recent enforcement actions involving antivirus vendor Avast, and location data providers X-Mode and InMarket. Europe, too, is moving in this area.
The US trade watchdog has decided that browsing and location data should be considered sensitive, and that – despite the absence of allegations about personally identifiable information (PII) within the datasets of the above businesses – what makes this stuff sensitive is what can be inferred from it.
"Years of research shows that datasets often contain sensitive and personally identifiable information even when they do not contain any traditional standalone elements of PII, and re-identification gets easier every day – especially for datasets with the precision of those at issue in the FTC's proposed complaints against Avast, X-Mode, and InMarket," the commission declared.
Two weeks ago, the agency resolved its complaint against security vendor Avast for $16.5 million based on allegations that the firm used a "a unique and persistent device identifier" with its Jumpshot analytics business to track internet users' activities – including "each webpage visited, precise timestamp, the type of device and browser, and the city, state, and country."
Despite the crackdown, data brokers continue to sell advertising data that threatens people's privacy.
Meanwhile, in Europe last week, privacy activist organization Open Rights Group filed legal complaints with data protection authorities in the UK and in France challenging data broker LiveRamp's "pervasive identity surveillance for marketing purposes." The org has asked data protection authorities to review LiveRamp's practices under Europe's GDPR and UK data protection legislation.
LiveRamp, when it was known as Acxiom, was one of the three data brokers that "openly and explicitly advertise data on current or former US military personnel," according to a 2021 report from the Cyber Policy Program at Duke University's Sanford School of Public Policy.
Even while helping to target visitors to Planned Parenthood with anti-abortion ads, selling data on US citizens to foreign companies, or selling data on US military personnel, these firms claim they don't sell personal information.
Nonetheless, data brokers – with the help of technology platforms like Apple and Google that provide location data – implement identifiers that can be used to infer personal information.
"The ad tech industry has been clinging to an unsustainable, narrow interpretation of what constitutes personal information," Arielle Garcia, privacy consultant with ASG Solutions, told The Register. "Given that this data is used to target, track, and profile consumers, there is a fundamental incompatibility between the use of identifiers and the concept of de-identification.
"Once someone interacts with an ad, for example, the alleged 'deidentification' is null and void. For example, one could purchase an audience segment of individuals likely seeking treatment for an illness, advertise to them, and have the ad drive traffic to a landing page (which [also contains a tracking pixel]), and a form where they are prompted to enter their name, and other personal information."
A report accompanying the Open Rights Group complaints looks at LiveRamp's identity graph system which, according to Wolfie Christl, a security researcher at Cracked Labs and report co-author, includes identity records on 250 million people in the US, 45 million in the UK and 25 million in France.
"It assigns everyone a unique personal identifier, the 'RampID', which is tied to their name, home address, previous addresses, email, phone numbers, device IDs (referring to their smartphones, tablets, TVs, browsers etc), account IDs at large platforms and IDs referring to digital profiles stored by other data brokers," wrote Christl in a post to LinkedIn.
RampID, the report alleges, allows businesses "to recognize, track, follow, profile and target people across the digital world." It further states that until recently "the terminology used by LiveRamp was misleading or could even be considered as deceptive," because it referred to RampID as an anonymous identifier. Presently, the company calls RampID a pseudonymous identifier – which is counted as personal data under GDPR, according to the report.
"Pseudonymous identifiers are identifiers, such as known identifiers that have been pseudonymized or device identifiers (such as a mobile device ID or cookie ID), that can't be directly tied back to an individual," LiveRamp's documentation states.
On the other hand...
Bill Budington, senior staff technologist for the Electronic Frontier Foundation, argues otherwise.
"Ad IDs provide a specific persistent identifier over multiple data points, so any data broker with a set of Ad IDs and location points can 'connect the dots' and trace an individual's movement over time," Budington told The Register. "Using that location data, further inferences can be made as to a person's home address, their workplace, who they have romantic relationships with, where they go after hours, etc.
"Any effort at anonymizing data has to adhere to rigorous standards," Budington added. "Just removing traditional identifiers such as name or SSN from a dataset isn't nearly enough. In fact, unique IDs which are assigned to an individual may be more identifying than a person's name."
"In combination, data sets that are linked with a device can be incredibly revealing and identifiable to a person, leading to pinpointing their location over time, sensitive locations they may have visited, and behavioral habits associated with location over time."
- American Express admits card data exposed and blames third party
- EU-turn! Now Apple says it won't banish Home Screen web apps in Europe
- Cops visit school of 'wrong person's child,' mix up victims and suspects in epic data fail
- White House goes to court, not Congress, to renew warrantless spy powers
Apple and Google implement a mobile advertising identifier, which is intended to be unique, user-resettable, and user-deletable, and can be used for geo-targeted marketing.
Technically non-persistent and notionally pseudonymous, these ad identifiers don't provide direct access to user profiles. But they can be linked to data profiles and can be used to target mobile devices with personalized ads based on location data.
Ad firms may or may not consider mobile IDs to be PII – depending on whether they can be used to identify the device user. Google's definition of PII, for example, is situational.
The ad giant doesn't consider pseudonymous cookie IDs, pseudonymous advertising IDs, IP addresses, or other pseudonymous end user identifiers to be PII for the purposes of its contracts and policies – even though laws in Europe, the UK, and the US may have different definitions that may apply and those definitions leave room for interpretation.
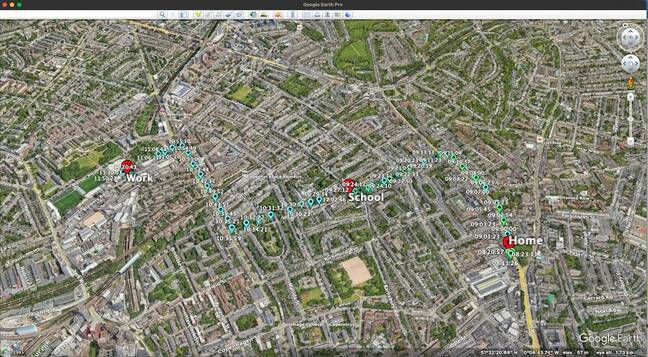
Ryan Paterson, president of privacy-focused mobile phone biz Unplugged, told The Register that he could approach a data broker and ask for all the advertising IDs in several geo-bounded regions – like the areas around a specific house, a school, and a restaurant – over a period of time.
Armed with this data, an individual or organization can build a map of a particular ad identifier's movements, which can often be used to identify the person using the device. If, for example, a particular identifier is often at a particular house in the evening, it's probably associated with that household. And if it also shows up often at a particular place of business during work hours, that person is probably employed there.
Paterson provided The Register with an example map of location data over time, using dummy data so as not to harm anyone's privacy.
Zach Edwards, security and privacy consultant with privacy research house Victory Medium, told The Register that while Apple and Google allow people to disable their advertising IDs, most people don't do that.
Mobile advertising IDs, he explained, apply to native iOS and Android apps – but not websites, which historically have involved different identifiers like HTTP cookies and IP addresses. But these often get combined.
"The IP address is often the join key," Edwards explained. "You have an IP address and an advertising ID on the mobile app side. On the website side or in-app browser side, you have lots of basically IP addresses. With in-app browsers, you also sometimes have the advertising ID [because the in-app browser exists within a native app]. Certain entities can buy lots of data appended to data that they have, and then really develop robust profiles for people. That's how a lot of the advertising segments are built. All the data brokers are exchanging data and building the best profiles they can."
Edwards also observed that there are advertising IDs beyond those offered by Apple and Google. Connected TV – content streaming through apps on smart TVs and set-top boxes – also comes with advertising identifiers.
"Apple and Google are the only two companies that have even a remote level of control and transparency around this," he noted. "The Tizen IDs and all these other TV IDs, these are on by default, hard to find how to turn it off, and the user is never prompted to turn it off. And that's becoming a bigger problem when every TV you can buy is like a big Android device."
Further compounding the problem, Edwards continued, is the fact that it's not obvious what the SDKs built into apps do with the data they handle.
"Neither Google nor Apple requires disclosure of SDK company names," explained Edwards. "So before you download an app, you may know what the permissions are. You may see their privacy label, but you don't know who their partners are."
It used to be that relatively few people knew how to exploit data effectively for identification and targeting. But now, once obscure gray-hat marketing techniques have become standard practice.
A decade ago, said Edwards, "only the highest level of government people were using ads for targeting people, serving malware to one person, like real pure fuckery on the ad networks. But now, there are large numbers of data brokers whose core offering is to track people as a service.
"We've basically crossed the Rubicon where every data scientist with even a little bit of experience with location data has in some way seen or is aware of these types of invasive practices." ®
Updated to add
In a statement to The Register after this story was published, a LiveRamp spokesperson told us:
From Chip War To Cloud War: The Next Frontier In Global Tech Competition
The global chip war, characterized by intense competition among nations and corporations for supremacy in semiconductor ... Read more
The High Stakes Of Tech Regulation: Security Risks And Market Dynamics
The influence of tech giants in the global economy continues to grow, raising crucial questions about how to balance sec... Read more
The Tyranny Of Instagram Interiors: Why It's Time To Break Free From Algorithm-Driven Aesthetics
Instagram has become a dominant force in shaping interior design trends, offering a seemingly endless stream of inspirat... Read more
The Data Crunch In AI: Strategies For Sustainability
Exploring solutions to the imminent exhaustion of internet data for AI training.As the artificial intelligence (AI) indu... Read more
Google Abandons Four-Year Effort To Remove Cookies From Chrome Browser
After four years of dedicated effort, Google has decided to abandon its plan to remove third-party cookies from its Chro... Read more
LinkedIn Embraces AI And Gamification To Drive User Engagement And Revenue
In an effort to tackle slowing revenue growth and enhance user engagement, LinkedIn is turning to artificial intelligenc... Read more